Objective
Deploy a secure PHP-based web application on Microsoft Azure to explore cloud infrastructure, DNS, SSL/TLS certificates, and web application firewalls (WAF). The goal was to gain hands-on experience in hosting, securing, and managing enterprise-level cloud applications.
Tools & Technologies
Azure App Services, Azure Front Door, Azure Web Application Gateway, Azure Key Vault, PHP 8 runtime stack, CSS, HTML, DNS configuration, IP management, nslookup/DNS lookup utilities, TLS/SSL certificates (self-signed & CA-issued), SSL offloading, Web Application Firewall (WAF), Linux (Ubuntu), Windows 10, CLI tools for Azure and Linux, basic traffic monitoring and logging
Implementation Process
Domain & Hosting – Deployed the application on Azure’s cloud infrastructure, configuring DNS and IP settings to make the site publicly accessible and globally available.
Tools/Skills: Azure App Services, DNS configuration, IP lookup (nslookup)
- Hosted the application under Azure’s free domain: emileeclements.azurewebsites.net.
- Configured and validated the public IP address assigned to the web app.
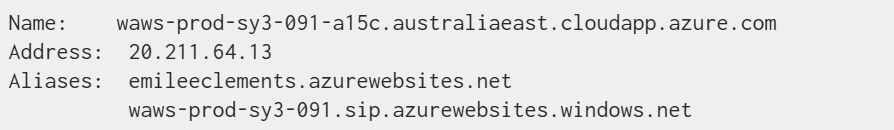
- Performed DNS record verification using
nslookupto confirm proper domain resolution. - Verified server location and connectivity to ensure global accessibility.
nslookup output:
Web Development & Front-End Assets – Organized and optimized project directories, static resources, and custom styling to deliver a responsive and user-friendly web interface.
Tools/Skills: PHP 8 runtime stack, CSS styling, file directory structuring, cross-browser compatibility, static resource management
- Selected the PHP 8 runtime stack in Azure App Services to handle backend functionality and server-side processing.
- Organized the project directory into /assets/css and /assets/images for clean file management and maintainability.
- Applied custom CSS styling to define the application’s user interface and ensure consistent rendering across browsers.
- Managed static resources (stylesheets, image files) to optimize client-side performance and enhance usability.
- Designed and implemented front-end elements that directly shape the visual appearance and user experience of the application.
Cloud Security & Access Controls – Implemented secure identity and access management through Azure Key Vault to protect cryptographic keys, secrets, and certificates while maintaining compliance.
Tools/Skills: Azure Key Vault, Identity & Access Management (IAM), access policies, auditing
- Configured Azure Key Vault to securely store and manage cryptographic keys, secrets (e.g., passwords), and certificates.
- Implemented access policies based on the principle of least privilege, restricting sensitive data usage to only authorized identities.
- Maintained audit compliance by enabling logging and monitoring of which users and applications accessed specific resources.
- Strengthened practical knowledge of IAM and cloud-native security services, including identity verification and trust establishment.
- Applied an understanding of the distinct security roles of each Key Vault object:
- Keys encrypt data in transit or at rest (symmetric/asymmetric cryptography, digital signatures).
- Secrets secure sensitive information such as credentials, only accessible to approved identities.
- Certificates authenticate users, devices, or applications, establishing trust between systems.
TLS/SSL Certificates – Configured and validated TLS certificates to ensure encrypted communication, trusted authentication, and secure certificate chain validation across browsers.
Tools/Skills: TLS/SSL, certificate authorities (CA), cryptographic trust chains, certificate management, DNS/subdomain security
- Compared self-signed certificates vs. CA-issued certificates, analyzing tradeoffs in cost, convenience, trust, and vulnerability exposure.
- Deployed TLS certificates in Azure (versions 1.0, 1.1, and 1.2), recognizing SSL 3.0 vulnerabilities and TLS as the modern secure standard.
- Verified certificate chain components: root certificates (DigiCert Global Root G2), intermediate certificates (Microsoft Azure TLS Issuing CA 05), and browser trust stores (e.g., Chrome → Baltimore CyberTrust Root).
- Evaluated wildcard certificates for securing domains and subdomains under a single binding.
- Strengthened understanding of cryptographic trust models and certificate lifecycle management (validity, expiration, renewal).
Web Application Firewall (WAF) – Strengthened application defenses with Azure’s WAF and Front Door services, filtering malicious traffic, enforcing access rules, and optimizing performance through SSL offloading.
Tools/Skills: Azure Front Door, Azure Web Application Gateway, WAF configuration, SSL offloading, Layer 7 security, geo-filtering
- Implemented Azure Front Door and Web Application Gateway to provide authentication, load balancing, and performance optimization.
- Configured SSL offloading to shift encryption/decryption workload from the application to backend servers, improving performance and centralizing certificate management.
- Applied Layer 7 filtering to defend against malicious traffic targeting the application layer.
- Enabled and tested OS File Access Attempt rule to prevent path traversal attacks by blocking suspicious URL patterns.
- Enforced geographic access restrictions (geo-filtering) to limit requests originating from Canadian IP addresses, while analyzing limitations such as VPN-based evasion.
- Strengthened understanding of how WAF policies and access controls complement each other in securing web applications.
Results – Deployed a secure, cloud-hosted PHP web application with optimized front-end performance, validated connectivity, and hardened security through TLS and WAF configurations.
- Successfully deployed a secure, cloud-hosted PHP web application accessible worldwide via Azure’s free domain.
- Implemented TLS encryption with a verified certificate chain (root + intermediate + browser-trusted) to ensure safe data transfer.
- Hardened application security through Azure WAF rules, SSL offloading, and Key Vault access policies, protecting against path traversal and unauthorized access.
- Optimized front-end performance by organizing CSS and image assets, improving load times and user experience.
- Validated DNS records and IP configuration to ensure reliable connectivity and availability.
Deliverables
Key Takeaways
- Gained hands-on experience deploying and managing enterprise-level cloud applications in Azure.
- Strengthened understanding of cloud security principles, including identity and access management (IAM), Key Vault usage, and access policy enforcement.
- Developed practical knowledge of TLS/SSL certificate management, certificate chains, and differences between self-signed vs. CA-issued certificates.
- Acquired skills in Web Application Firewall (WAF) configuration, including Layer 7 filtering, rule testing, and geo-blocking considerations.
- Improved project organization and front-end asset management for scalable, maintainable web applications.